Python 0bf
You don’t need to deobfuscate the Python, but that’s up to you. ;-;
Attachments
Recon
Although the provided Python script has been obfuscated using an online tool, we can still analyze its structure. By assigning meaningful names to its variables and functions and reorganizing the code, we can better understand how the obfuscation works:
import base64
import zlib
deobfuscate = lambda code : zlib.decompress(base64.b64decode(code[::-1]))
exec(deobfuscate(b'contents'))
The script looks quite straightforward, all we need to do is reverse the bytes, decode them using base64, and then decompress the result with zlib.
Exploitation
Although there are several ways to approach this, the fastest is likely to use CyberChef with a straightforward recipe that performs all three operations in sequence.
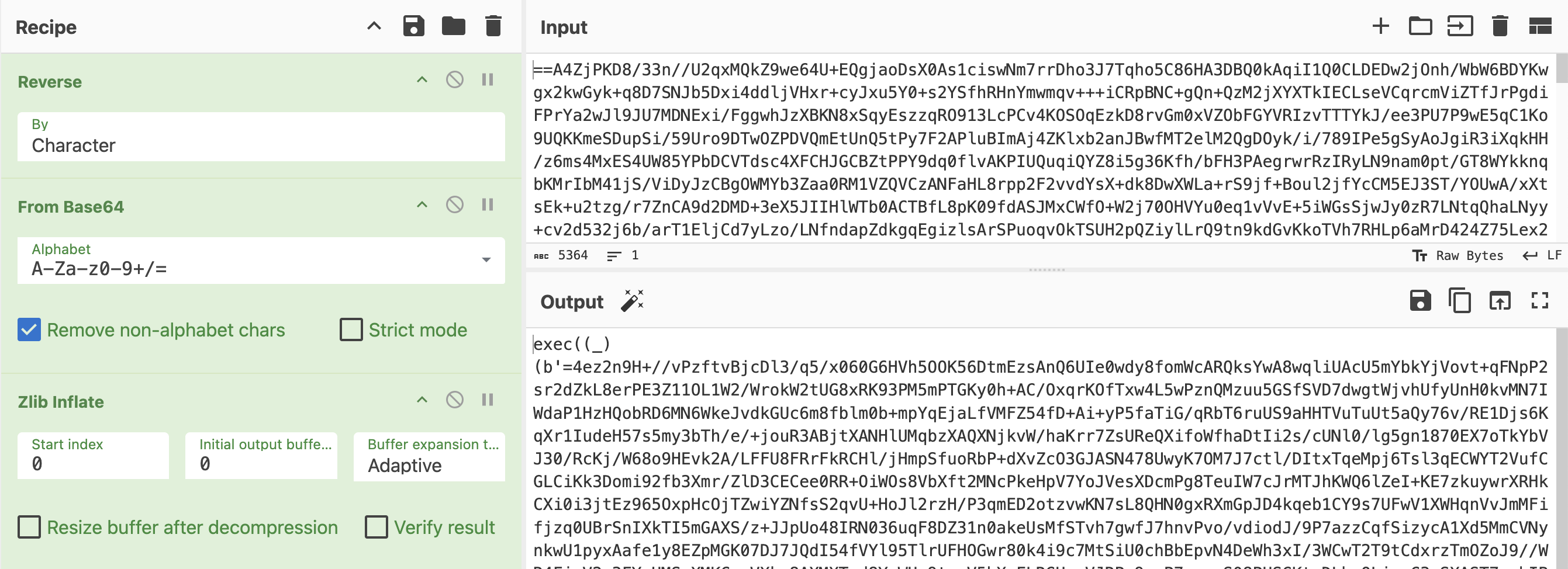
Unless, of course, someone with a particularly devious mindset has created a recursive obfuscator that repeatedly re-applies the same obfuscation process.
Flag capture (the hard way)
In fact, this is not a problem for us. If you are not familiar with it, CyberChef includes flow control operations. Using these, we can create simple loops and other programming constructs.
All we need to do is repeatedly apply these three operations until we obtain a valid flag. This recipe in CyberChef accomplishes this almost instantly.
flag = "v1t{d4ng_u_kn0w_pyth0n_d3bugg}"
inp = input("Input the flag: ")
if (inp != flag):
print("wrong")
else:
print("correct")
There is no need to run the code at all!
Flag: v1t{d4ng_u_kn0w_pyth0n_d3bugg}
Flag capture (the easy way)
Alternatively, we can refer to the challenge description, which suggests that deobfuscating the original Python script is unnecessary.
Indeed, this is correct. We can simply execute the script within an interactive Python REPL to retrieve the flag:
$ python
>>> import obs
Input the flag: no idea
wrong
>>> dir(obs)
['_', '__builtins__', '__cached__', '__doc__', '__file__', '__loader__', '__name__', '__package__', '__spec__', 'flag', 'inp']
>>> obs.flag
'v1t{d4ng_u_kn0w_pyth0n_d3bugg}'